Ping Identity SSO
Set up Ping Identity Single Sign-On (SSO) on Sentry.
If you change your organization slug, you'll need to make the same update in the steps where you enter the SAML configuration values.
Log in to Ping Identity.
Go to the "Adminstrators" environment for your organization.
If you don't require a permission group for Sentry, skip to step 5.
In the sidebar, click on "Identities", then "Groups", and navigate to it. From there, create a new group and add yourself and other members to it. For more details about group creation, see the Ping ID docs.
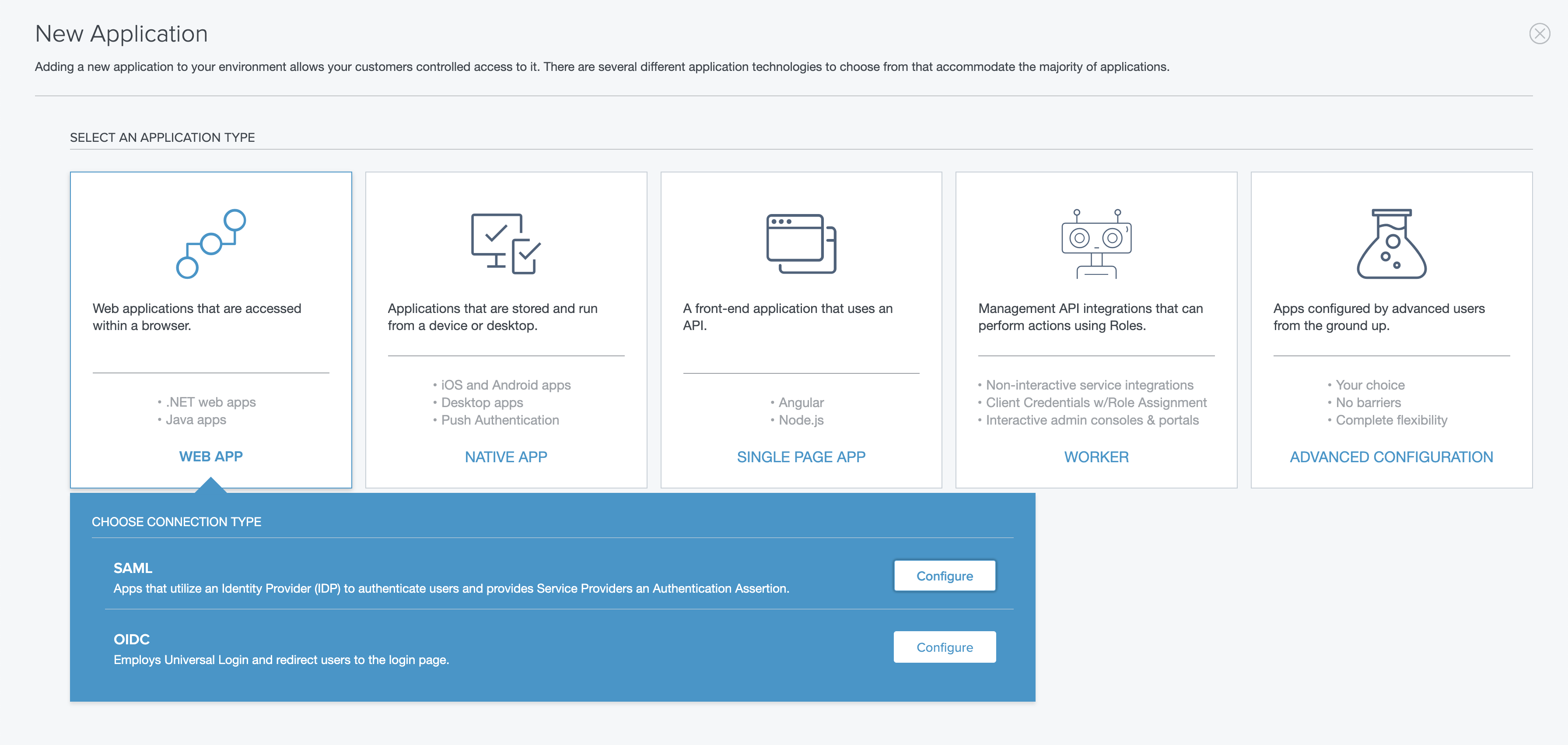
In the sidebar, click on "Connections", then "Applications". Click on "+ Application" and for the application type, select "Web App" and "SAML".
For section (1), labeled "Create App Profile", you can get the Sentry logo from here.
For section (2), labeled "Configure SAML", select "Manually Enter". Enter the following data in each line and save your changes.
Assertion Consumer Service (ACS) URL:
https://sentry.io/saml/acs/YOUR_ORG_SLUG/Entity ID:
https://sentry.io/saml/metadata/YOUR_ORG_SLUG/Single-Logout (SLO) Endpoint:
https://sentry.io/saml/sls/YOUR_ORG_SLUG/Target Application URL:
https://sentry.io/organizations/YOUR_ORG_SLUG/
In section (3), labeled "Attribute Mappings", for "Application Attribute" ← "Outgoing Value", use:
saml_subject←Email addressemail←Email addressfirst_name←Given Namelast_name←Family NameYou can use custom key values, but you will need to amend the steps below. For more details about advanced attribute mappings for custom configs, see this guide from Ping ID.
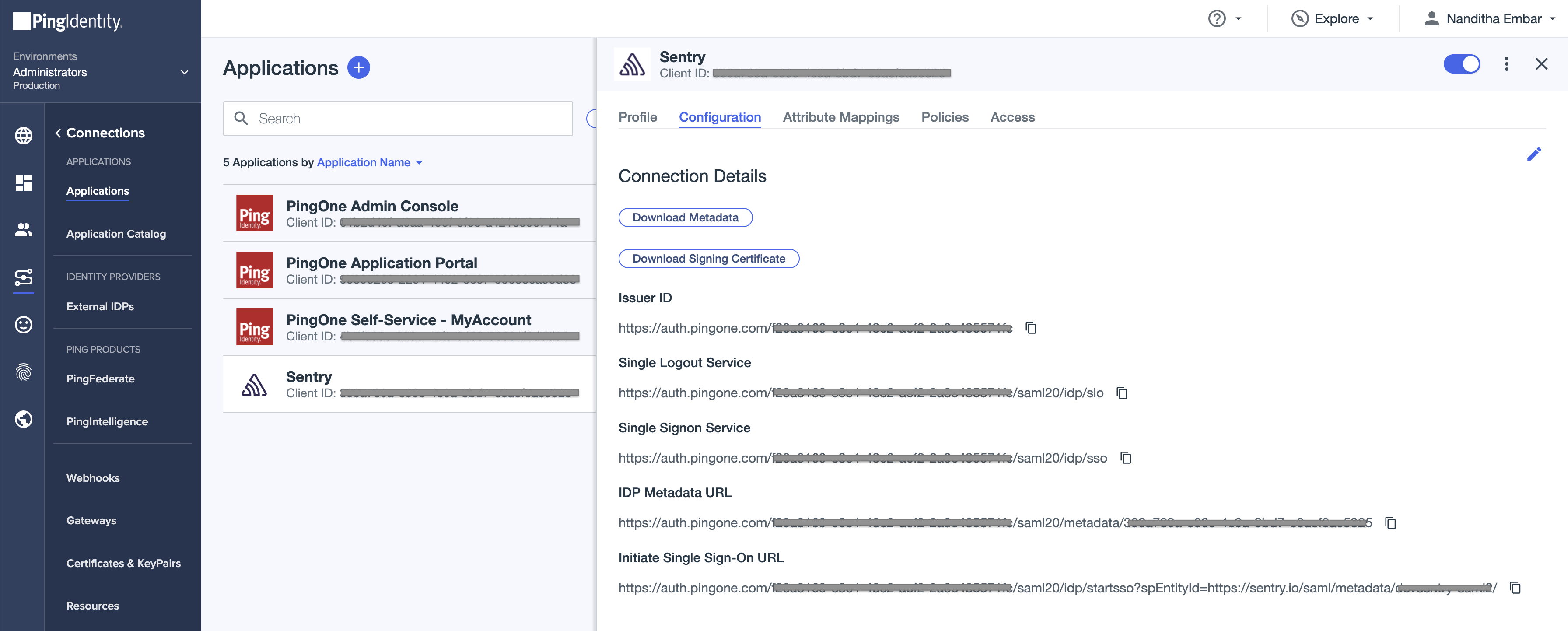
Once the application is created, click on the Sentry application and navigate to "Configuration" and copy "IDP Metadata URL". This URL will be used in the subsequent step on Sentry.
Go back to Sentry. Navigate to Settings > Auth (or go to
https://sentry.io/settings/YOUR_ORG_SLUG/auth/) and click on "Configure" for SAML2.Paste the IDP Metadata URL from above and click "Get Metadata".
On the next page, enter the following keys in their respective fields to map the Ping ID attributes to Sentry, and then save them:
IdP User ID:
saml_subjectUser Email:
emailFirst Name:
first_nameLast Name:
last_name
Sentry will attempt to authenticate and link your account with Ping Identity. After successful authentication, you'll be redirected to Sentry's SSO configuration page, where you can take the following actions:
You can share the "Login URL" value, which will be used for SP-initiated SSO, with the users in your organization.
Scroll down to the bottom and ensure that "Require SSO" is checked if you want to enforce logging in with Ping.
Set a "Default Role" for new SSO users. Selecting "Member" should cover most use cases.
If you made changes, click "Save Settings" to complete your setup.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) or suggesting an update ("yeah, this would be better").